Identity Threat Prevention
Executive Summary
Cybersecurity has reached a turning point. Although organizations have invested heavily in authentication, detection, and response systems, most breaches still originate from compromised identities rather than failed firewalls or misconfigured endpoints. Attackers now exploit tokens, sessions, and behavioral blind spots more quickly than detection can respond to them.
Traditional tools detect and respond after a breach occurs. Identity Threat Prevention (ITP) secures protection before any compromise happens. By applying cryptographic validation to every identity, device, and session, ITP shifts identity checks from passive credentials to active, self-verifying security measures.
The result is a security approach focused on prevention — it blocks credential theft, session hijacking, and MFA bypass before they happen, without creating user friction or operational difficulties.
The Problem: Reactive Security is Failing
The industry’s reliance on detection and response creates an endless loop of chasing threats that have already succeeded. Since Identity is the new attack surface and MFA fatigue is real, SOC teams are overwhelmed, and users experience friction even as gaps persist. Detection tells you what happened. Prevention ensures it never does.
What Is Identity Threat Prevention?
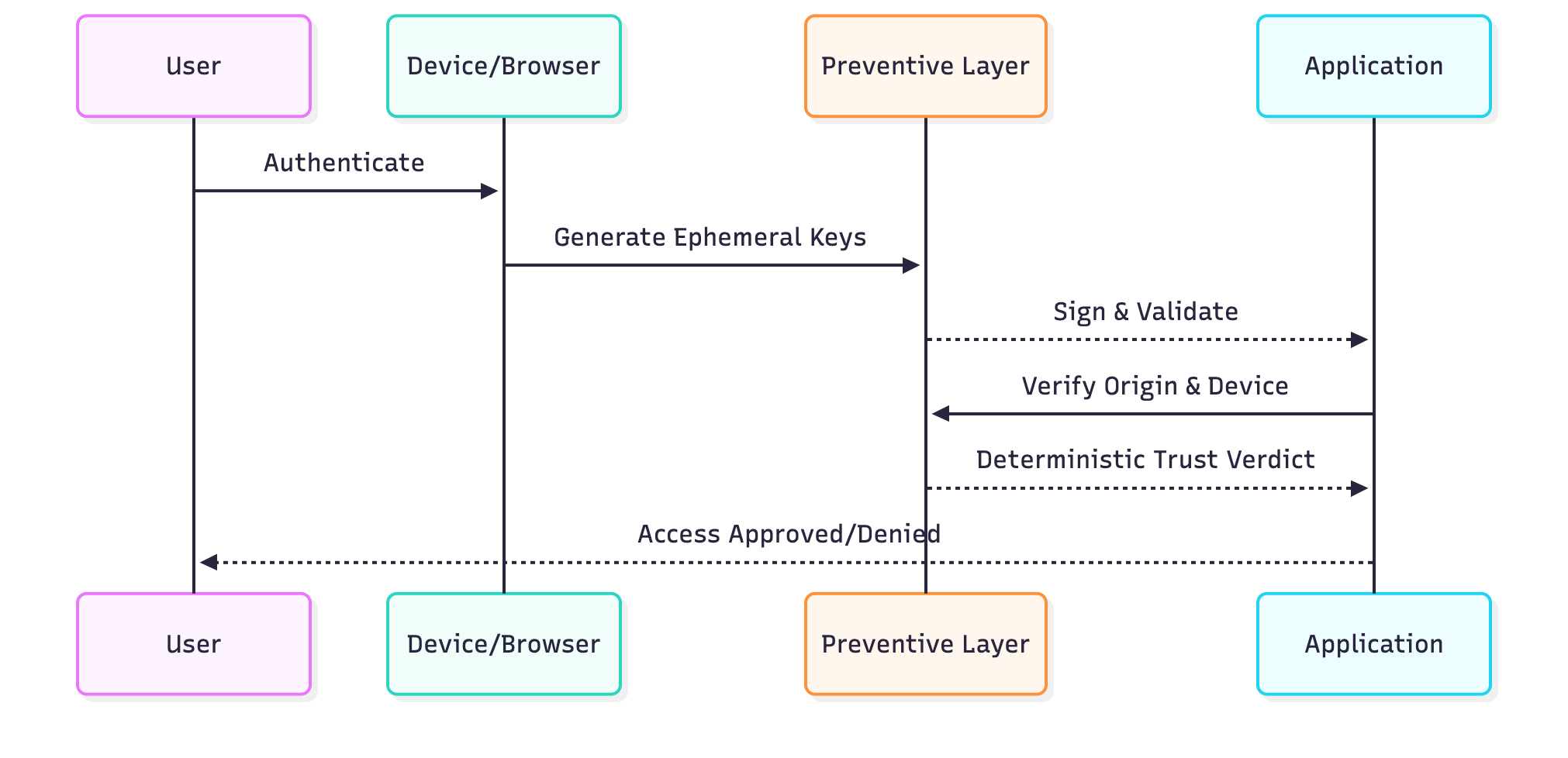
Identity Threat Prevention (ITP) is a modern security discipline that continuously validates digital trust at the session and transaction level, and not just at login. It ensures that every credential is cryptographically validated, every session remains bound to a legitimate device and origin, and every access decision is binary: trusted or denied.
Instead of depending on probabilistic risk scoring or behavior analytics, ITP enforces deterministic trust by providing verifiable proof that a session, device, and identity are legitimate.
Deterministic Trust: From Probability to Proof
Traditional identity systems rely on probabilistic risk assessments, where a user's legitimacy is judged based on indirect context and behavior signals. Deterministic trust replaces this guesswork with cryptographic proof, providing a definitive yes or no for each validation, thereby removing ambiguity and ensuring consistent enforcement. Key aspects of deterministic trust include binary trust models, ephemeral cryptographic keys, binding to devices and origins, continuous enforcement, and automated, impartial validation. This approach ensures that decisions are consistent, verifiable, and free from human influence error.
Why Identity Threat Prevention Matters Now
Identity has become the enterprise control plane. MFA alone can’t defend against token replay or adversary-in-the-middle attacks. With cloud-first operations and hybrid work, browsers have become the new perimeter. Without continuous validation, identity remains a soft target. ITP fixes that by cryptographically linking identity to device and context.
ITP also helps organizations meet compliance and Zero Trust mandates requiring continuous identity assurance and verification at every access event.
How ITP Works
ITP enforces cryptographic validation at every request. After the initial authentication, session tokens are bound to the device and origin metadata. Each request is revalidated in real time, ensuring that only legitimate sessions persist. If an anomaly occurs, the session is revoked instantly. This happens regardless of the technology in use, such as Okta, Ping, or other identity providers.
The Business Case for ITP
Implementing ITP produces measurable improvements in security posture, operational efficiency, and user experience. Organizations may report significant reductions in account takeover attempts, password resets, and false alerts. Beyond measurable ROI, ITP offers strategic value by establishing a verifiable Zero Trust foundation, simplifying audit reporting, and boosting customer confidence in identity-driven systems.
Why Now: The Urgency for ITP
Attackers are evolving more rapidly than traditional detection systems can keep pace. Credential misuse, MFA fatigue, and session hijacking have become everyday issues. Security teams can no longer depend only on reactive measures. Implementing ITP today gives organizations a lasting edge, lowering credential attacks, improving compliance, and turning identity into a strong perimeter secured by cryptographic methods.
See what’s new with the ITP bootcamp.
Conclusion
Identity Threat Prevention (ITP) represents the future of identity security. It closes the gap between authentication and assurance, making every session verifiable, every credential defensible, and every access provably trusted. In a world where detection will always lag behind attack innovation, ITP provides prevention at the identity edge — ensuring that trust itself becomes unbreakable.